So, you have a Crypto Wallet and you want to know the best way to keep it secure, right? Well before we dive into that, let’s make sure you understand exactly what a Crypto Wallet is!
Structuring Your Crypto Wallet for Maximum Security

What is a Crypto Wallet?
A Crypto Wallet is a digital wallet that stores your public & private keys and allows you to send, receive and store cryptocurrency. While cryptocurrency is actually stored on the blockchain, your private keys give you access to your cryptocurrency from within your wallet. Your keys prove your ownership of the wallet and allow you to make transactions.
Upon creating a new wallet there are a few things you need to pay attention to. Let me explain them in a little more detail:
Public Key: Your Public Key is an alphanumeric string which acts as your wallet ‘address’. This address is shared with others so they can send you cryptocurrency. Think of your Public Key like your email address, it’s fine for others to know and is required when they need to send you an email.
Private Key: Your Private Key is also an alphanumeric string, but it is much longer than your public key. This should never be shared with anyone. Think of your Private Key like the password to your email address. If someone knows your Private Key, they can access, manage and steal your cryptocurrency.
Recovery Phrase: Also known as a Seed Phrase or Mnemonic Phrase, a Recovery Phrase is a list of 12, 18 or 24 words that store all the information needed to recover your private keys in the event you lose them. This is never to be shared with anyone and needs to be written down and stored offline in a safe place. If someone knows your Recovery Phrase, they can recover your crypto wallet from anywhere and steal your cryptocurrency.
So to summarize, your crypto wallet stores your public and private keys. Your public key is used to receive funds while your private key is used to sign transactions and access your funds. If you lose your private key, you can use your recovery phrase to restore your wallet.
Digital or Hardware Wallet?
When storing your cryptocurrency most people use a combination of Digital Wallets and Hardware Wallets. But what is the safest method?

The Hardware Wallet, commonly referred to as a cold wallet, is currently the most secure method to store your crypto. This is because it’s 100% offline. The private keys always remain offline and even when transacting with online platforms, the private key signs transactions inside the device. If the device is lost, you just use your recovery phrase to restore your private keys on a new Hardware Wallet.
Think of the Hardware Wallet as a bank vault. If you want to withdraw something from the vault you need to physically unlock it and take it out. If you want to withdraw crypto from your Hardware Wallet, you need the physical device to approve the transaction.
Crypto stored on a Hardware Wallet is entirely under your custody and control.
The Digital Wallet, commonly referred to as an online wallet, is what most people use as they are the simplest way to get started and offer a good balance of security and easy access. They are usually created within an app like Metamask or other software like Exodus. This method comes second to using a hardware wallet.
When you create an account on a Centralized Exchange like Binance, you are also provided with public keys allowing you to send and receive crypto. This is another method that a lot of people use to store their crypto.
The problem with this is that the Exchange controls your private keys. You do not receive a recovery phrase when you create an account on a Centralized Exchange. This should not be used to store your crypto as it is not in your custody.
This method can be used as an onramp for you to convert fiat into crypto and then sent to a wallet that you have full control and custody over.
Now that we’ve cleared that up, how do we best protect our wallets from potential security threats?
Different Ways to Protect Your Wallet!
Below are a list of steps you can take that ensure you always have security at the forefront of your mind:

- Keep your recovery phrase private and ensure it is protected from being damaged. One way to do this is by purchasing something like a Cryptosteel Capsule and storing it safely somewhere offline. Never put your recovery phrase on a computer or a device that can connect to the internet.
- Create complex passwords using letters, numbers and symbols. This will severely reduce the chance of successful cyber-attacks if your wallet is targeted.
- Spread your crypto assets among multiple wallets. This will reduce your risk if your wallet is ever compromised.
- Enable two-factor authentication if the option is available. This adds an extra layer of security that needs to be bypassed.
- Never use public wi-fi when connecting your wallet or approving transactions. Make sure the network you are connected to is private and trustworthy.
- Do not engage in any trades or swaps unless they are conducted through reputable and trustworthy platforms such as Foxyswap and Sudoswap.
- When interacting with secondary marketplaces ensure you only use reputable platforms and double check the token address to avoid buying anything fake.
- Always disconnect your wallet from websites once you have finished using them.
- When sending cryptocurrency to another destination, always double check you are sending it to the correct address on the correct blockchain.
- Always be cautious of free airdropped tokens that are sent to your wallet. Never click links and always confirm if the airdrop is official or a scam. If it is a scam then send these to a burn address, never sell them to anyone – it’s unethical.
- In most cases, keep any software up to date. Ensure you understand what the updates are before installing them.
- Consider creating a fresh wallet after a set time and transfer all your assets over. This reduces the risk of any prior security issues you may not have known about and gives you peace of mind.
- Before approving any transactions, make sure you read and understand what exactly it is that you are approving. Failure to do so could result in third parties gaining access to important information or worse, having your wallet drained.
- Configure your wallets with an effective structure that ensures both security and efficient management of your funds.
Having a proper structure for your wallet configuration is incredibly underrated when it comes to keeping your crypto safe. So let’s dive into that a little deeper.
How to Effectively Configure your Wallet Structure?
Configuring your crypto wallets with an effective structure that ensures both security and efficient management of funds can be challenging and is often overlooked by newer investors. Let’s take a look at the diagram below and understand why an investor might use this configuration:
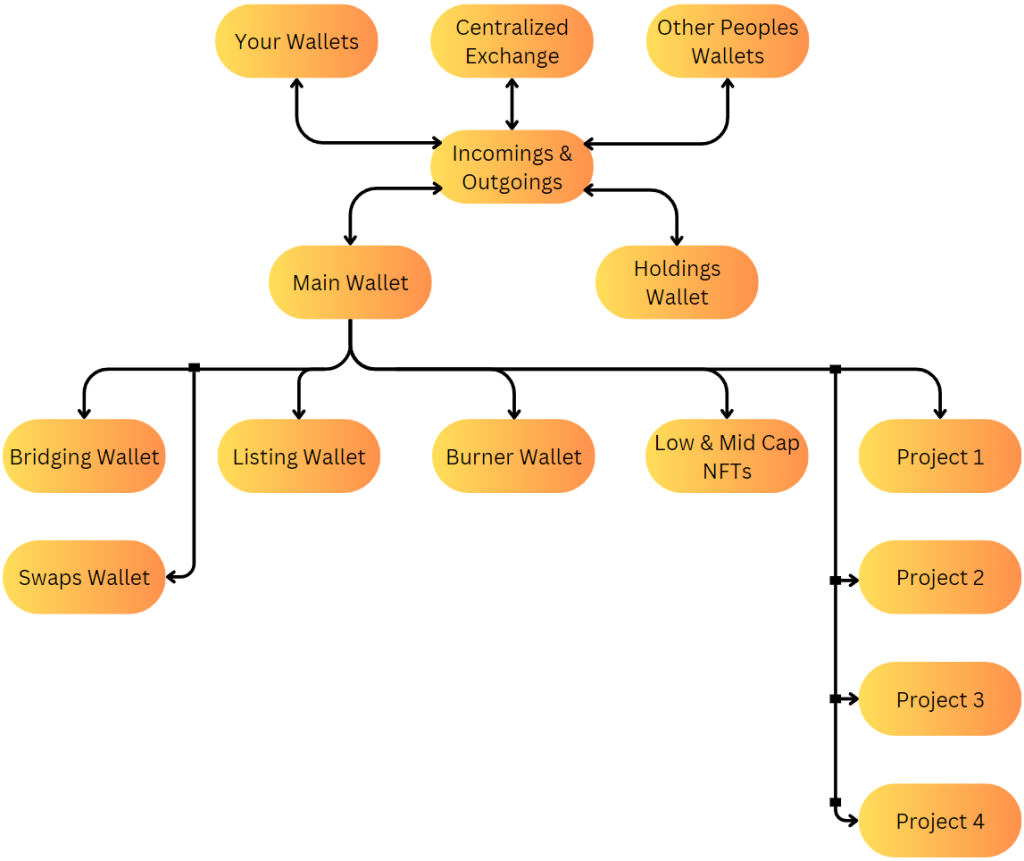
- Your Wallets: This is any other wallets you may own.
- Centralized Exchange: This is any accounts you have on a centralized exchange like Binance, OKX, Swyftx, Bybit, etc.
- Other Peoples Wallets: This is any other wallet you may interact with that is not controlled by you.
- Incomings & Outgoings: This is soley used as a pass-through wallet. Any funds coming into or out of these wallets need to go through this first. This leads to easy tracking of transactions. This wallet is never connected to anything.
- Main Wallet: This is the main wallet that will communicate with all your other sub-wallets.
- Holdings Wallet: This is where you store all your crypto that you are holding. This wallet is never connected to anything and should be linked to a hardware wallet.
- Bridging Wallet: This wallet is used specifically for bridging tokens across different blockchains. This is only ever connected to bridging websites.
- Swaps Wallet: This wallet is used for any token swaps you perform. This is only ever connected to token swap websites.
- Listing Wallet: This wallet is used for listing tokens or NFTs for sale, reducing the risk of accidentally listing something you didn’t intend to. This wallet is only ever connected to trusted secondary marketplaces.
- Burner Wallet: This is used for specifically minting new tokens or NFTs. Get into the habit of creating fresh Burner Wallets every now and then.
- Low & Mid Cap NFTs: This is used to hold random lower-value NFTs and prevents clutter in your other wallets.
- Project 1, 2, 3, 4: These are wallets to hold specific NFT collections that are considered high value. This wallet is never connected to anything other than trusted project specific facilities.
By having separate wallets, you are preventing unnecessary exposure of your main assets and making it a lot easier to monitor and track your transactions.
Remember, it is crucial to maintain high security standards for each wallet. Where you see fit, always use a hardware wallet, use unique passwords and never share your private keys or recovery phrase.
Oh, and one last thing:
If something seems too good to be true, it probably is.
If there not your Keys, it’s not your Crypto.
Stay safe out there!


